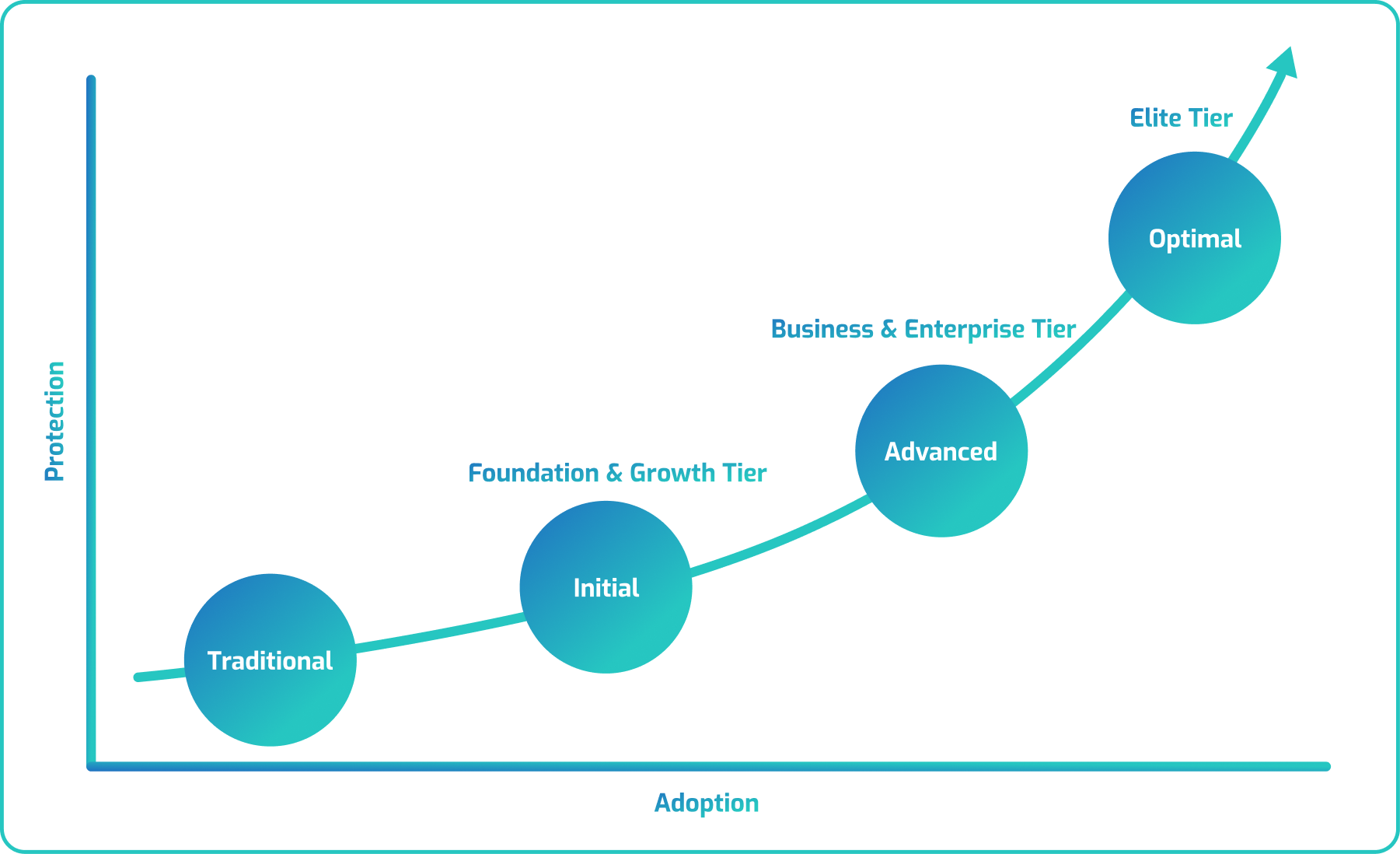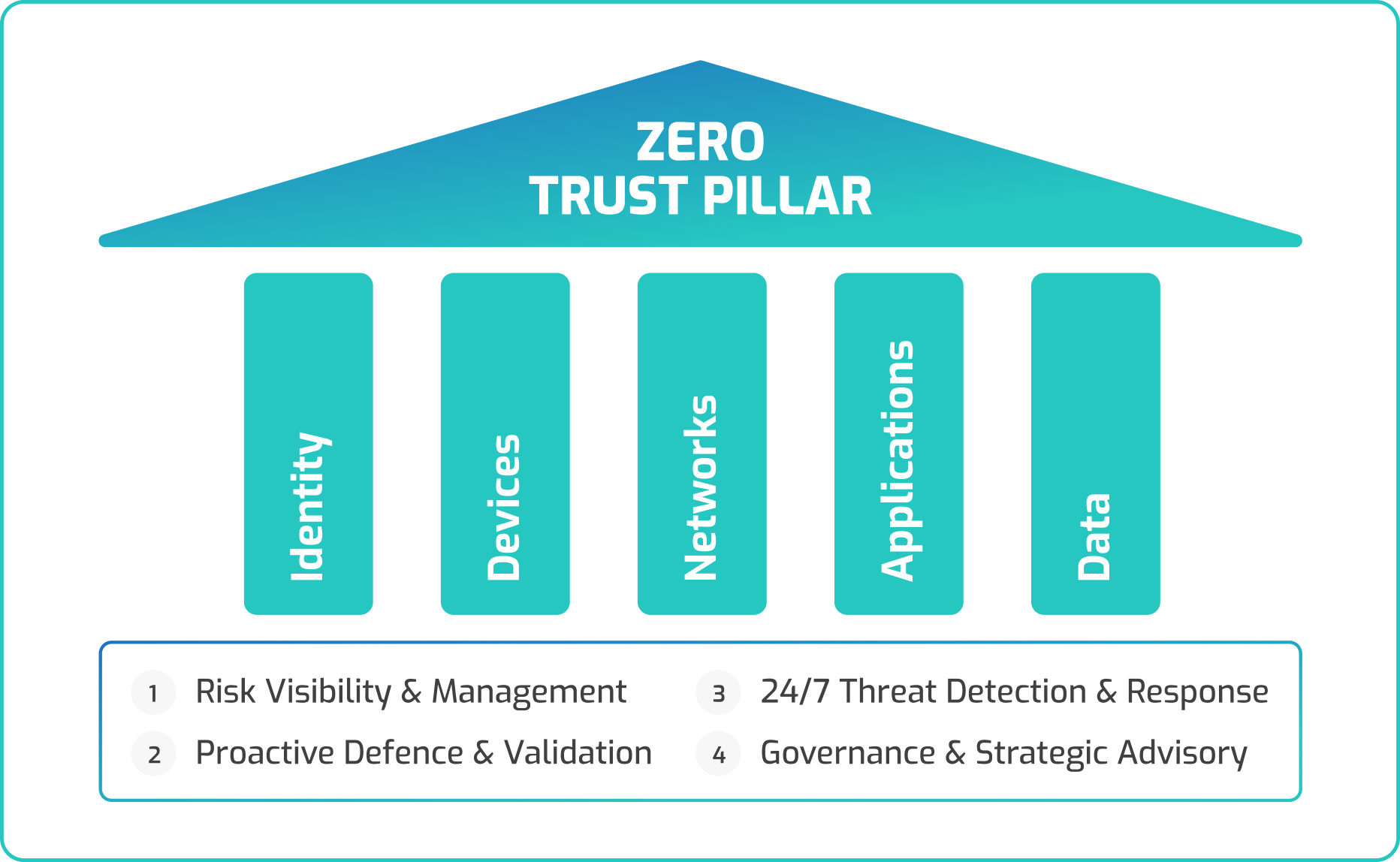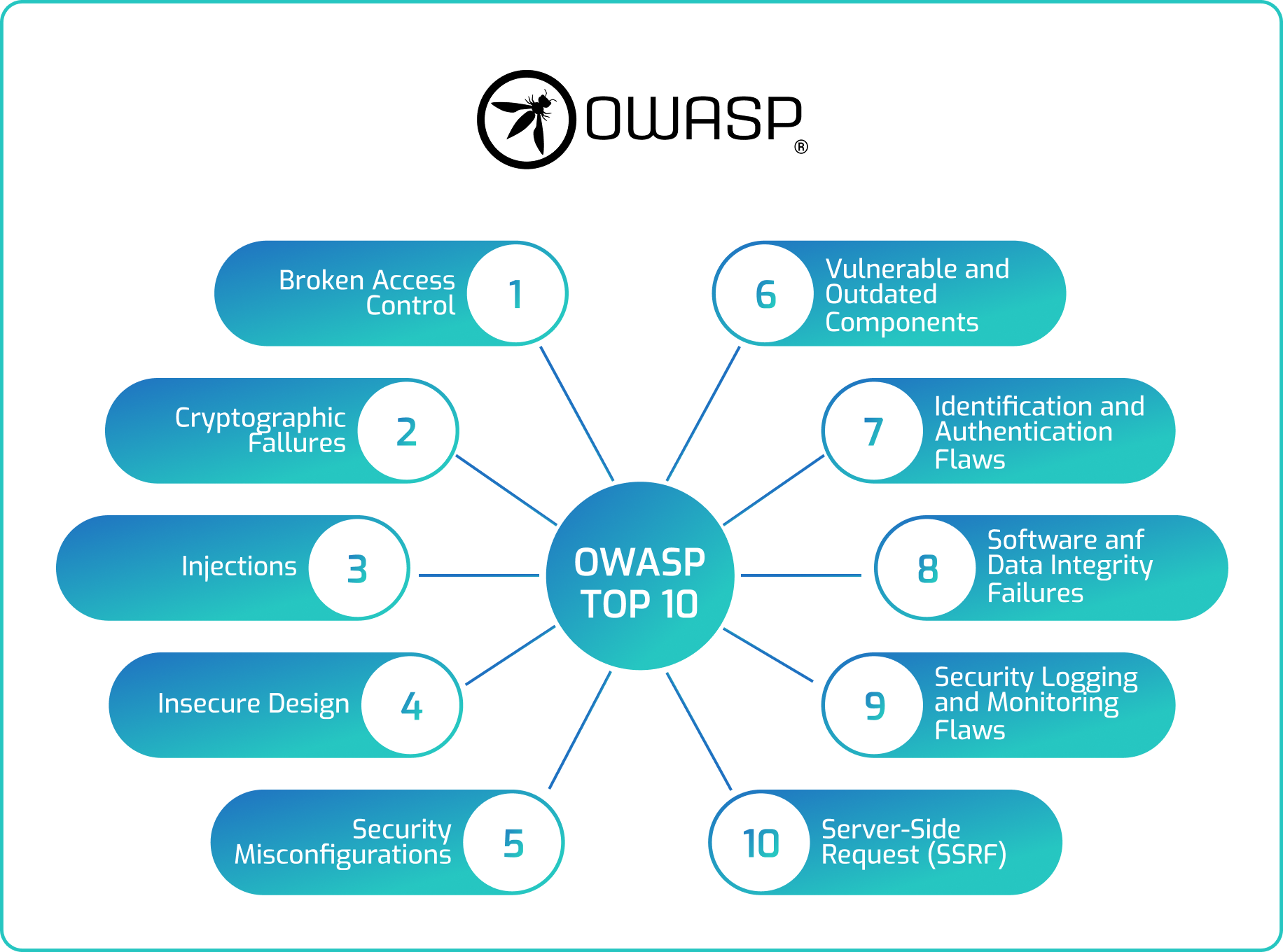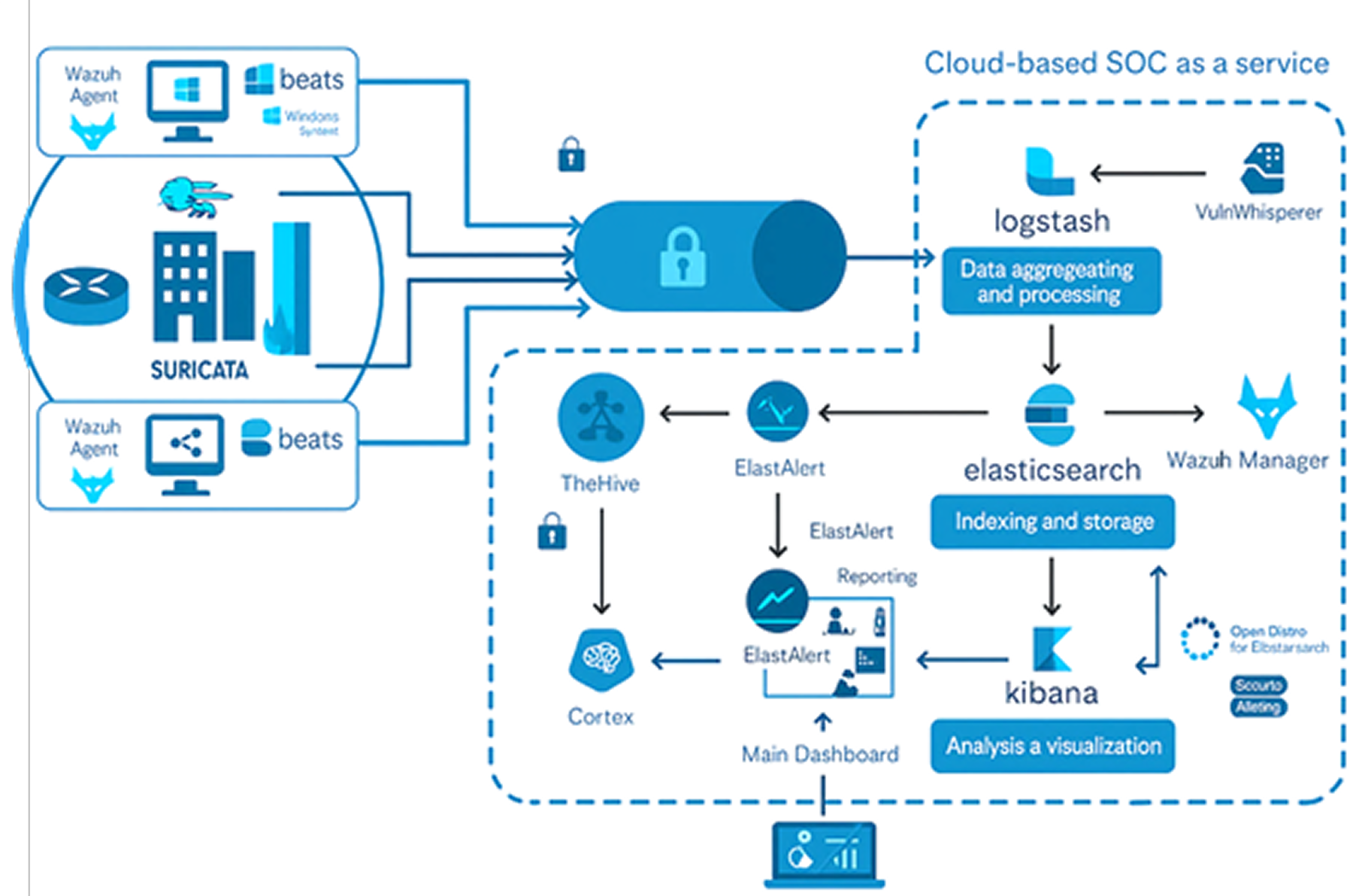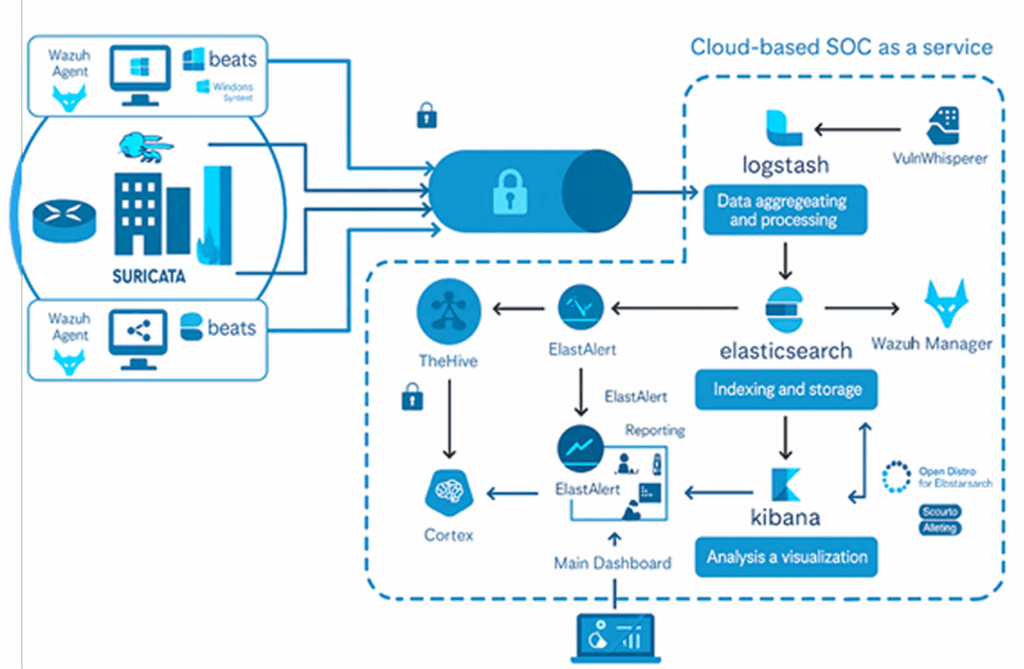
vCISO360™ is CyberShield’s full-spectrum cybersecurity leadership service, combining strategic oversight with hands-on execution to strengthen your defense from every angle.
This flagship service ensures real protection through continuous compliance alignment, active SOC governance, deep testing, and security awareness. Powered by CyberShield’s certified experts, threat intelligence, and always up-to-date playbooks tailored to evolving risks, your business is safeguarded.